Trend Micro uCTF 2024
---
This writeup will be covering **Trend Micro Careers Philippine’s University Capture the Flag** challenges which includes both from the qualifier round and the finals round.
In this Online CTF, our team ranked 5th out of 187 teams in the qualifier round and 15th out of 30 teams in the finals. I will try to be concise as much as possible while explaining the solving process.

Note that some challenges in this competition are not included here in the writeups for umm... various reasons which may include
* I forgot what the instruction was (lol)
* I accidentally deleted the challenge file (bruh moment)
* Maybe I’m still working on it (really)
This is a running list of writeups! I’ll add more in my free time! Last updated Sept 10
[=] QUALIFIERS
================
Aug 30
* * *
Warm Up
=======
Cryptography
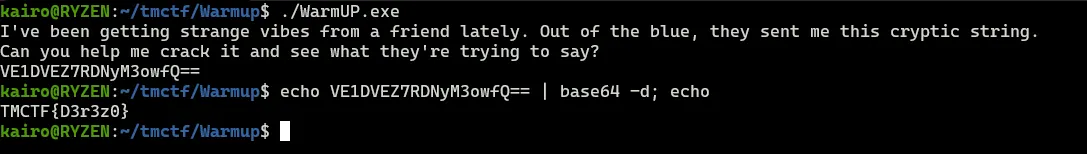
We receive a **WarmUP.exe** file. When running the file, it says that we have to crack a certain string. We notice it’s a base64 encoded string so we just decode it to get the flag
One Friend
==========
OSINT

A single image named **OneFriend.png** is given to us. Our goal is to find what the name of the building that the picture is taken at. Running the command **exiftool** reveals that it has metadata that tells us where that picture was shot.
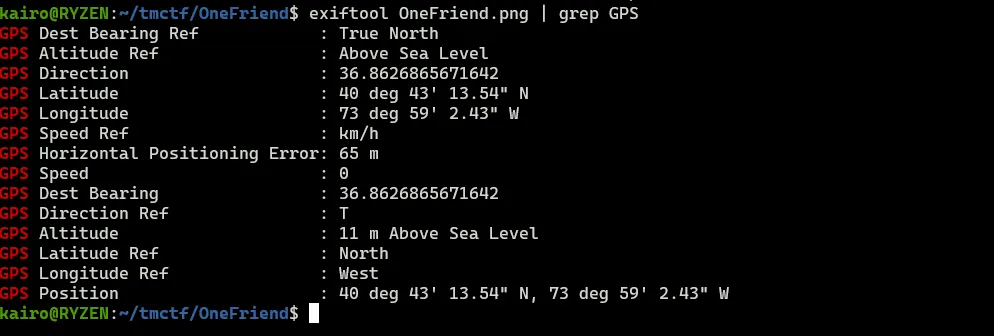
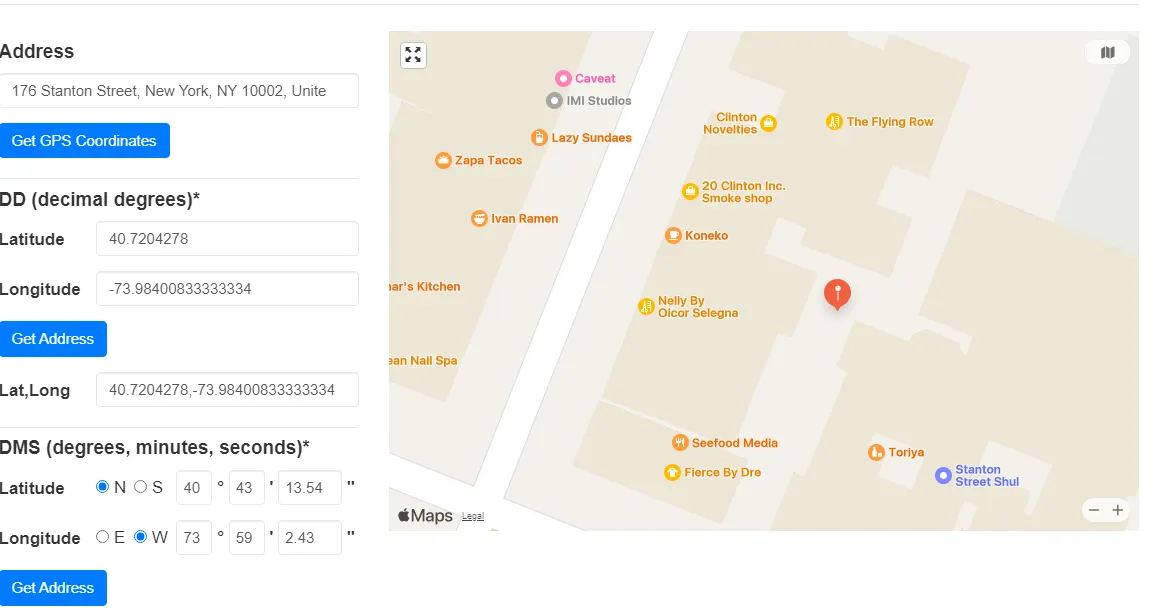
Though there are multiple buildings surrounding the pin, we notice that it may be this cat cafe named _Koneko_ since the picture also shows a cat.
Red Lanterns
============
OSINT

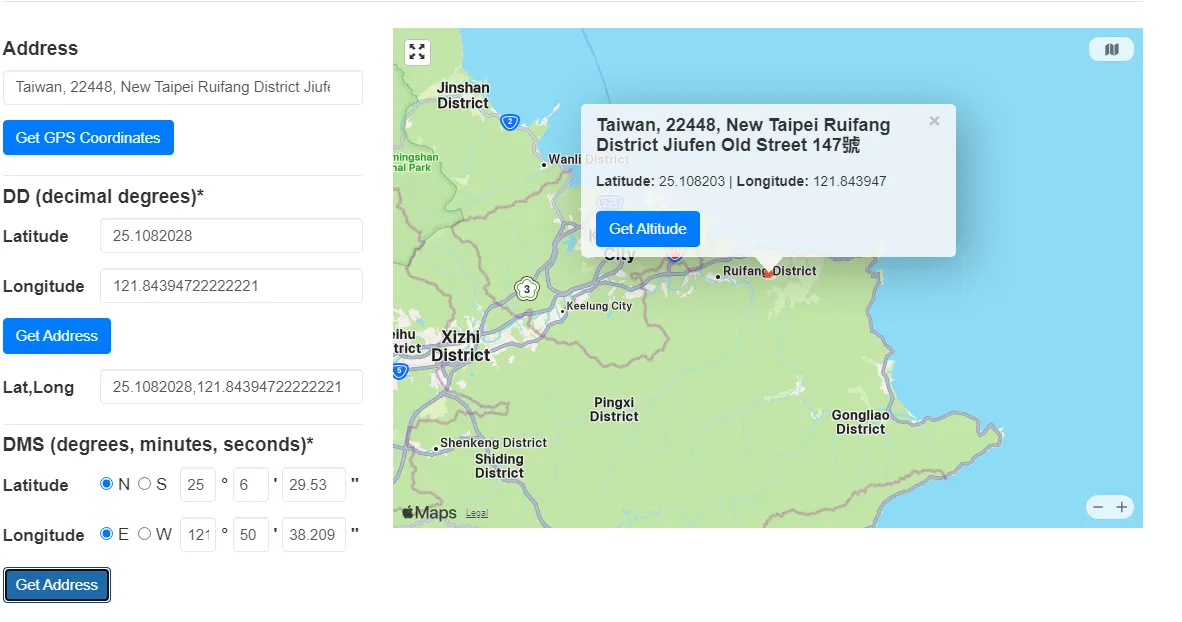
Given an image **RedLanterns.jpg**, we have to look for the city where this image is taken. Again similar to the challenge above, there is also a GPS Position metadata.
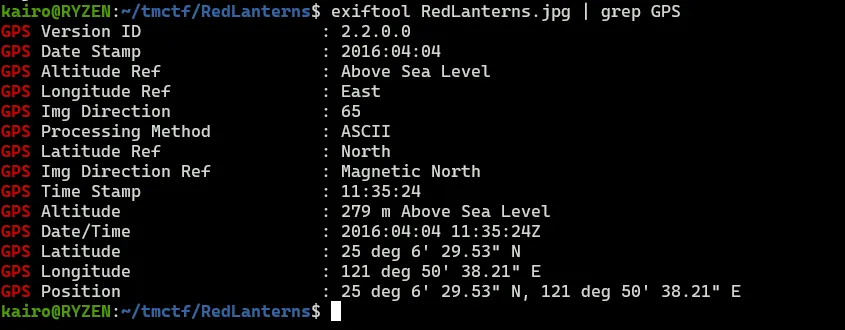
The picture also shows a tagline: _“FuFa Shoes since 2004”_, when searching for it, you find results of a Taiwanese shoe company. But since we already have the GPS Position let’s just use that instead of doing lengthy OSINT.
Magic Key
=========
Forensics
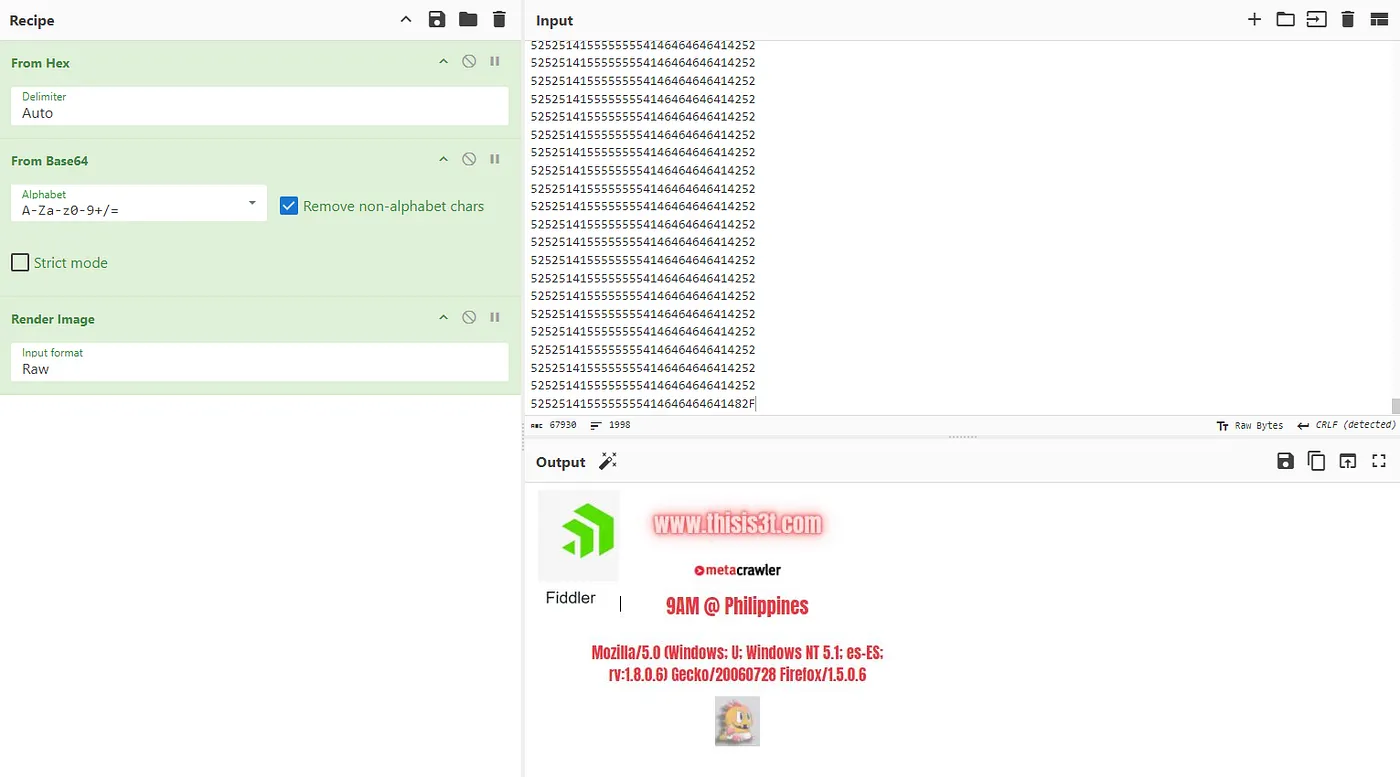
A single text file **MagicKey.txt** seems to contain multiple lines of hex where our goal is to retrieve the website. We hop on **Cyberchef** to decode it easily.

The magic feature in **Cyberchef** claims it is HTTP chunks, it is just being silly, when we manually decode it from hex we notice that it is a base64 encoded image!
Emergency Message
=================
Forensics
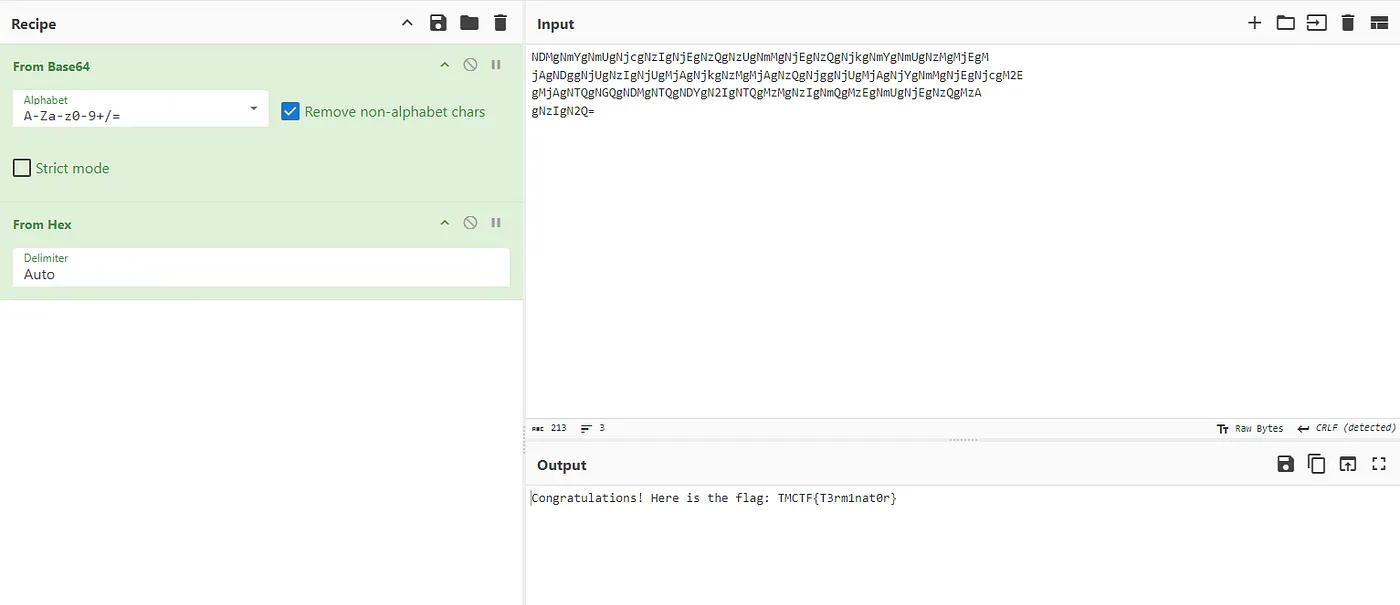
We have an image, let’s retrieve the flag!

We can use websites to extract the text from the image and decode the base64 text. Be careful though as some websites extracting text from image sometimes mistake similar looking characters like l, 1 and I, 0, o and 0, et cetera. Using **Cyberchef** we see that the decoded base64 is hex, decoding it further reveals the flag.
Hidden Payload
==============
Forensics
We’re given a hidden\_payload.pcap and our task is to retrieve a website link which has the flag. Firing up our Wireshark we see a network traffic consisting of just an HTTP request and response.
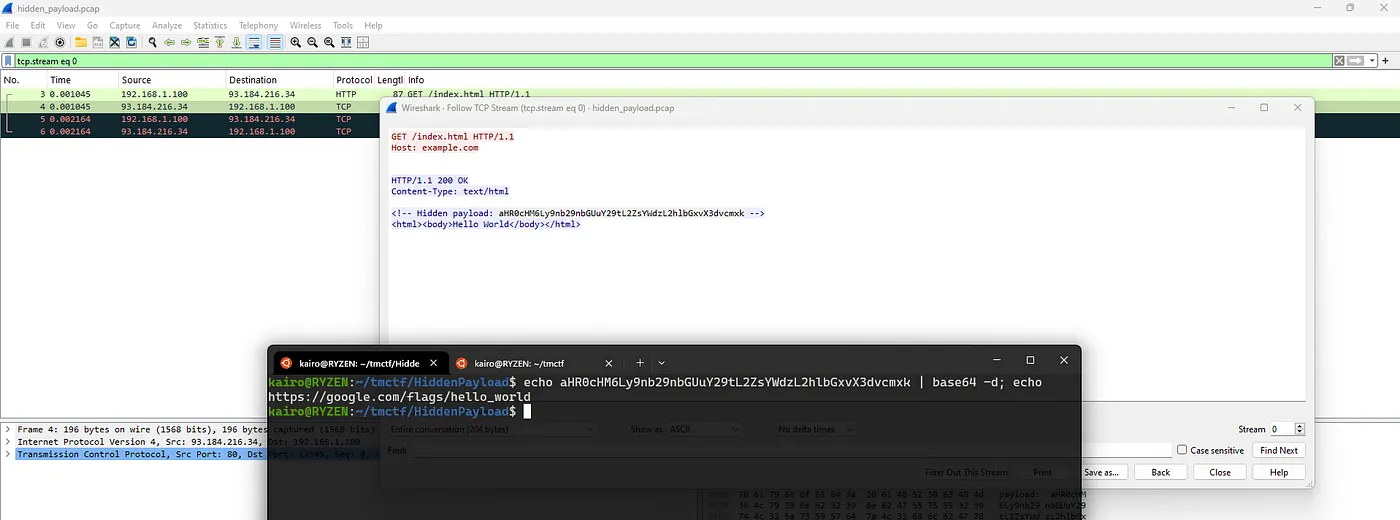
The website contents has an HTML comment that has an encoded base64, decoding it shows us the website link which is also the flag.
Mission Impossible
==================
Reverse Engineering
A binary file named MissionImpossible.exe is provided to us. It’s an executable for Windows so let’s try running it.
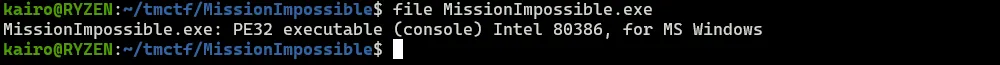
When running the file in Windows, the results says that a certain mission has failed and it stops.
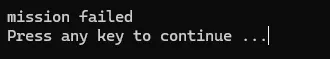
I checked for strings inside the binary if there’s anything useful, and I notice a file in a directory that doesn’t even exist on my PC. If that file doesn’t exist and it says mission failed, then surely mission successful if it exists?
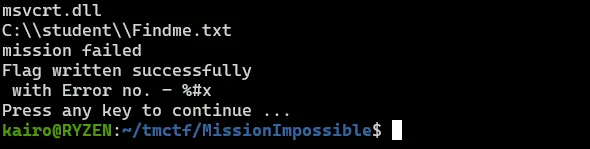
I immediately created a directory with the file and finally , we get the flag
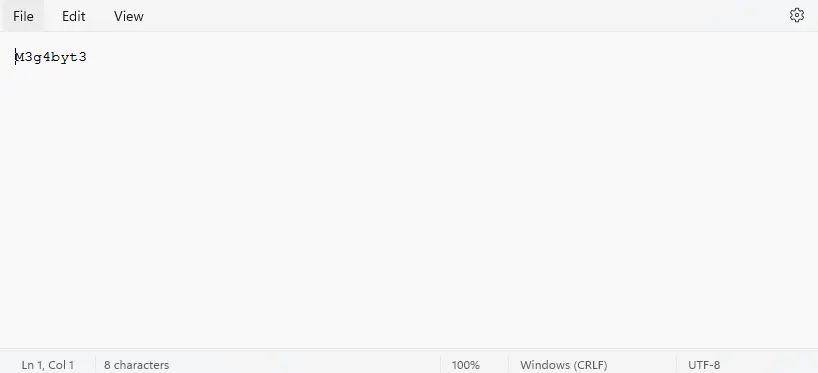
Cryptic Sound
=============
Forensics
A file named CrypticSound.wav is given to us. It’s just tweeting birds but something sounds off!
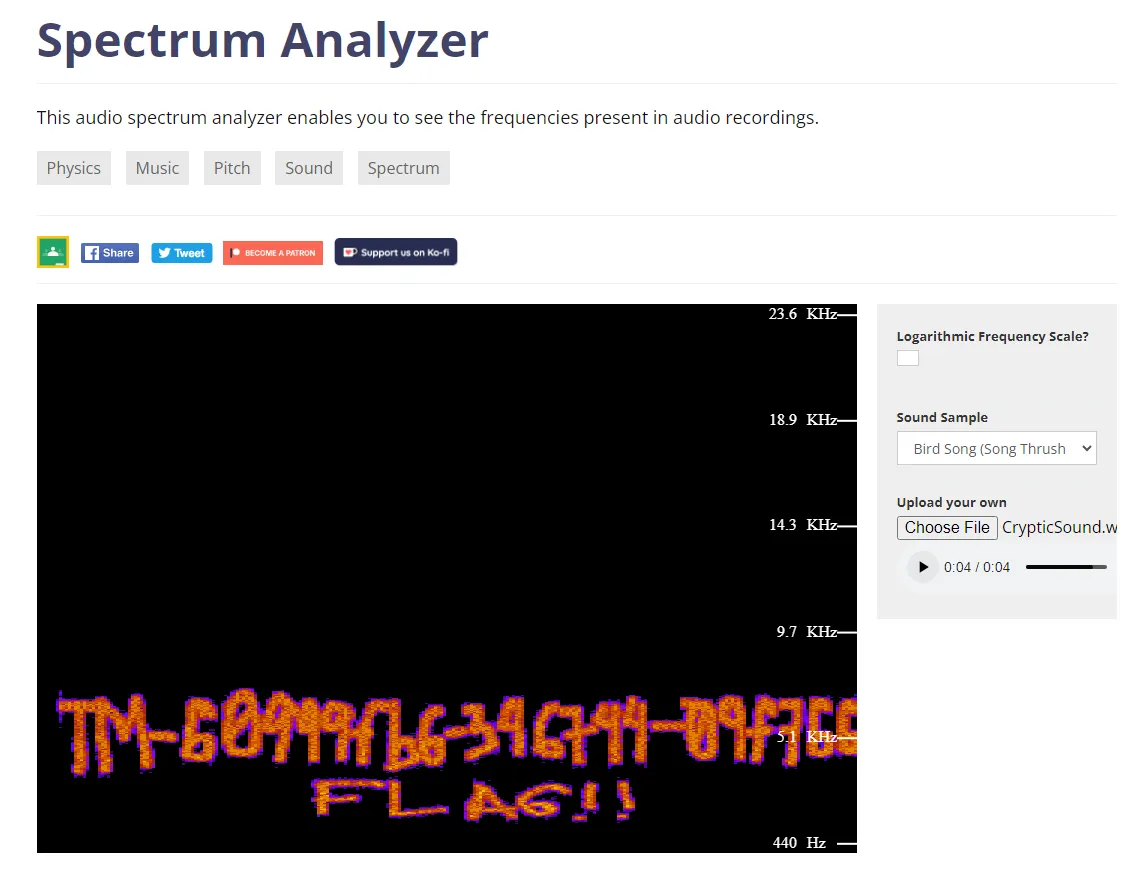
Didn’t know it was that obvious.
Lost Passport
=============
Forensics
A woman said that she lost her passport, the airline gave her a soft copy of her documents, but I don’t think she knows how to open these kind of stuff. Let’s help her. We’re given a **lp.e01** file which is an Encase Image format
By using a command-line tool named ewf-tools to handle these kind of files, we mount this encase file to a directory, and there we can see the contents of this file.
ewfmount lp.e01 output # make sure output directory exists
mount output/ewf1 -o ro,norecovery /mnt # mount to /mnt
cd /mnt # results are here

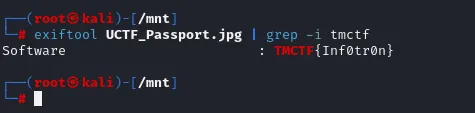
We don’t see anything particular when we open **UCTF\_Passport.jpg**, looking at its metadata using **exiftool**, we see the flag.
Breaking the Seal
=================
Forensics
We receive a password-protected BreakingTheSeal-encrypted.pdf file.

Let’s get the hash of this file using pdf2john and crack it using password crackers. I love using **hashcat** as it’s really fast.
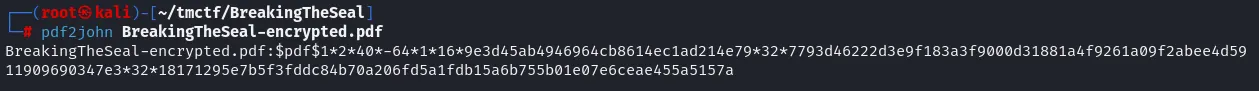
I copied the hash and pasted it ina file named **hash**, then we run **hashcat** and use rockyou.txt as our wordlist (In Kali, it’s located at /usr/share/wordlists/rockyou.txt.gz).
hashcat -a 0 hash /home/kali/wl/rockyou.txt
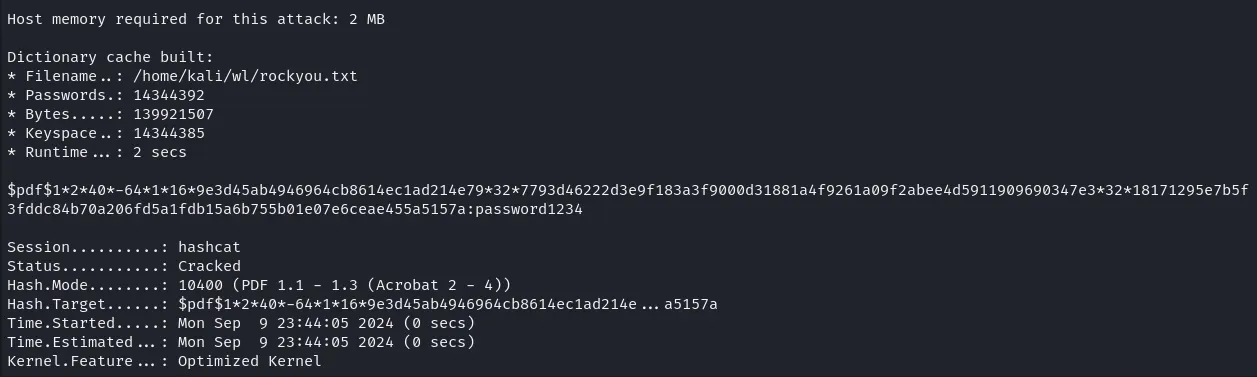
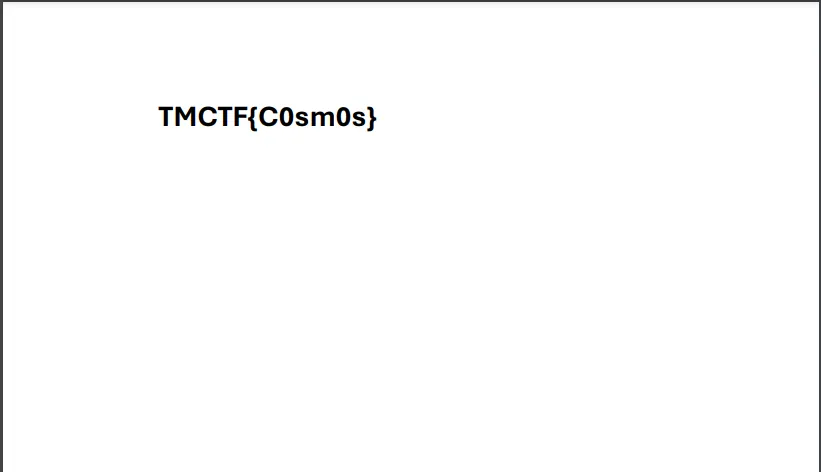
In 2 seconds we find out that the password is **password1234**. After entering the password, we open the pdf file and retrieve the flag.
The Seven Gates
===============
Reverse Engineering
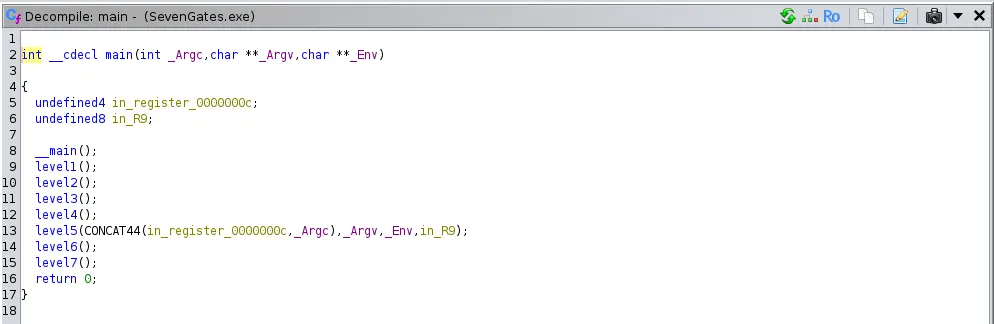
We receive a Windows executable named **SevenGates.exe**. It seems to be asking for 7 passwords until you can get the flag. In the competition, we tried analyzing the hex bytes of the binary and retrieved 2 passwords.

We couldn’t find the third password, so we just fired the binary into **Ghidra**. In the main function we see 7 different functions that handle the password verification of each level.
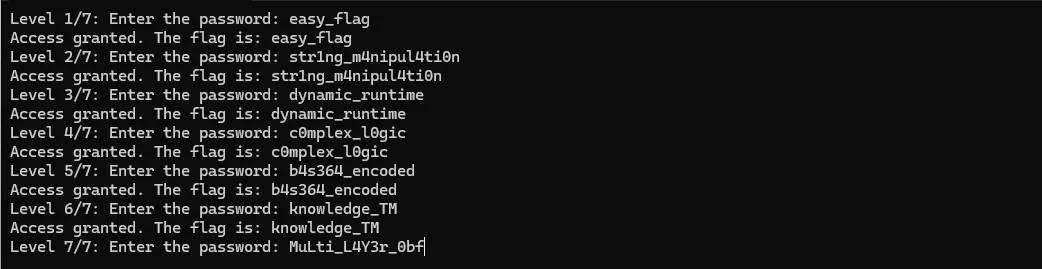
We’re only after the flag anyways so let’s analyze the last level. In level7 function we see that the flag is in local\_98 and the password is in local\_108 which is a combination of local\_98 and local\_90. It is encrypted twice using XOR cipher first using the key 0xAB then (adding 5, then) 0x5F. When the correct password is supplied which is MuLti\_L4Y3r\_0bf, The **printf** function prints local\_98 first, without a null terminator it also reads local\_90 which has the null terminator at the end essentially making the final password and flag the same value.
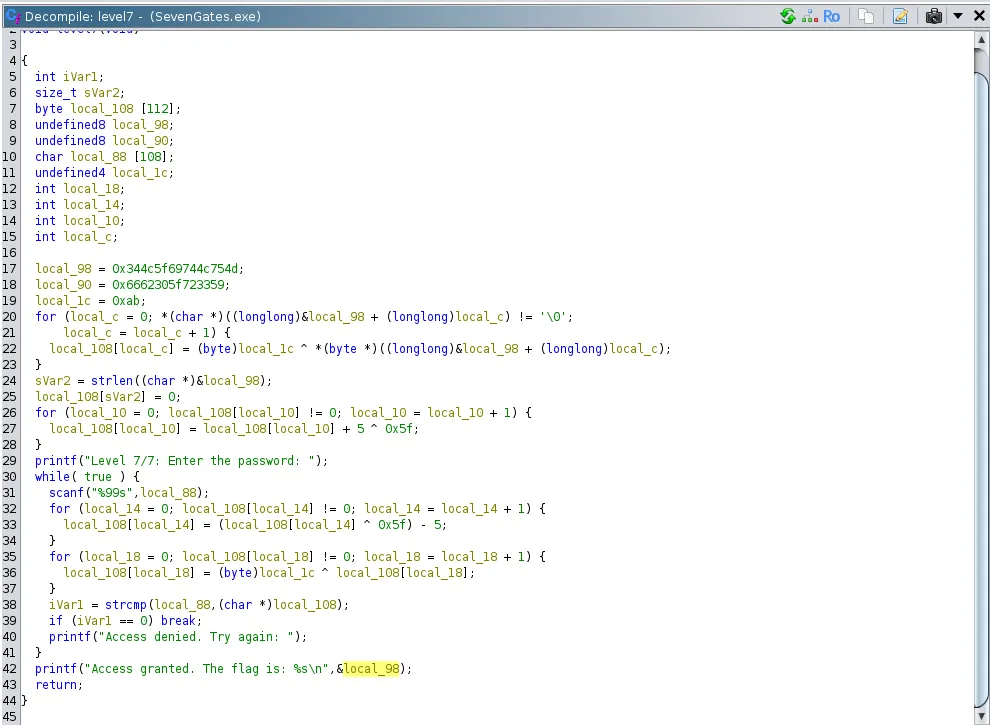
I reverse engineered the other functions to get the passwords, I won’t be showing exact steps, since we got the flag already but here it is:
* Layer 1: easy\_flag (visible in hex dump)
* Layer 2: str1ng\_m4nipul4ti0n (2 values in hex dump concatted)
* Layer 3: dynamic\_runtime (generated by a separate function)
* Layer 4: c0mplex\_l0gic (XOR encrypted but visible in hex dump)
* Layer 5: b4s364\_encoded (flag copied to another var, still visible in hex dump)
* Layer 6: knowledge\_TM (visible in hex dump)
* Layer 7: MuLti\_L4Y3r\_0bf (reverse engineered)
After submitting Layer 7, the program ends and closes without prompt.
[=] FINALS
============
Sep 03
* * *
Hello World
===========
Forensics

We are given an empty **Hello\_World.docm** file which is a Microsoft Word 2007+ document. We unzip it to unpack its components and **vbaProject.bin,** which is a macro, catches our attention.
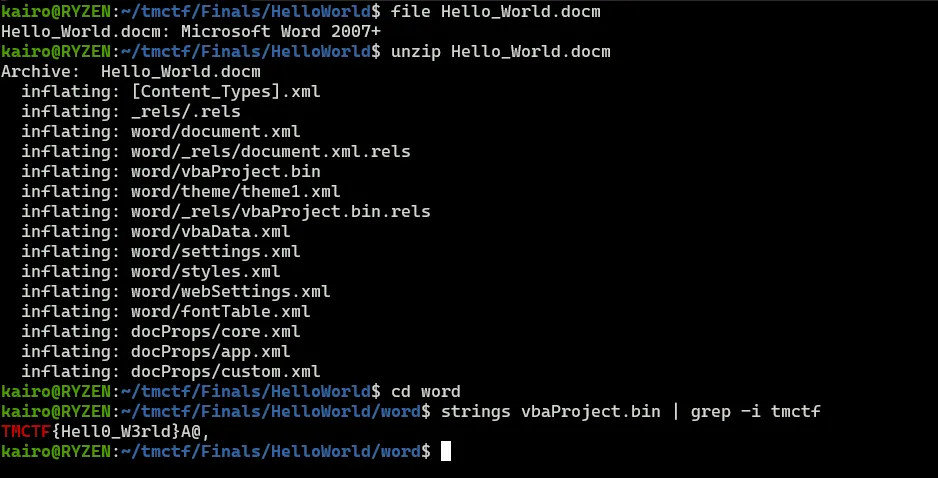
We look for the flag inside the macro and there we find the flag.
Buried in Bytes
===============
Forensics

We’re given a pdf named Buried\_In\_Bytes.pdf which just has some lyric in it. When opening the pdf file, I notice this opens:
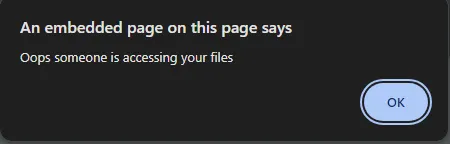
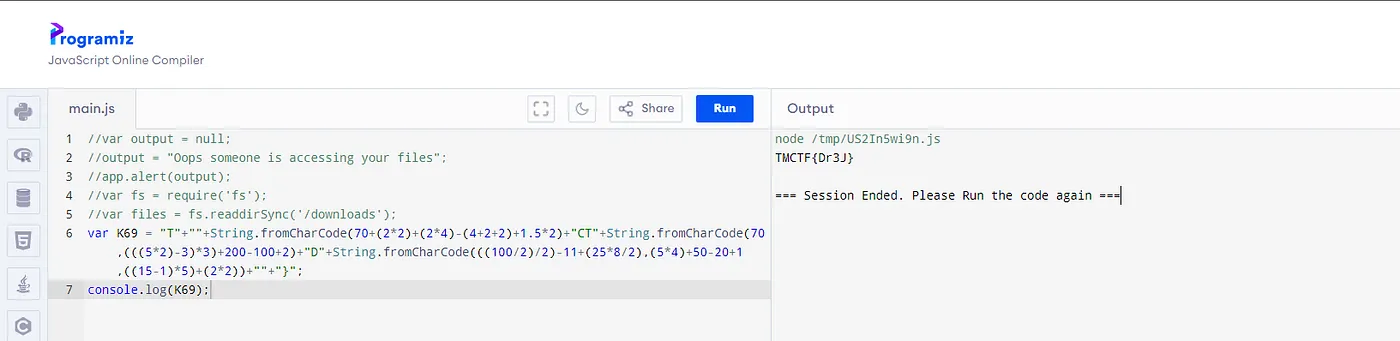
So I thought there may be an embedded script here, so I went and ran **strings** command on the pdf file and indeed there is an obfuscated JavaScript code.
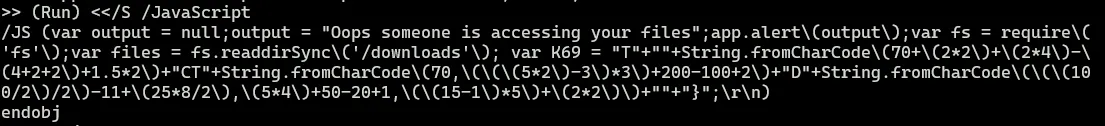
So I cleaned up the code and commented out lines that aren’t necessary.
Untangled
=========
Forensics
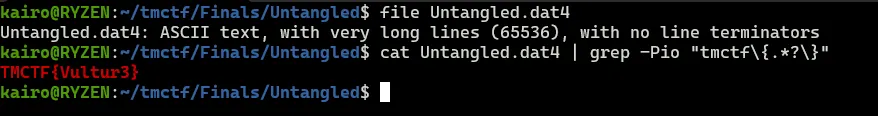
This one is quite simple. The flag is just hidden in a bunch of characters. Simply grepping it won’t do the trick as there is no line breaks so grep just outputs the entire file. Combine **grep** with regex and show exact match shows us the flag
Obfuscated Trail
================
Forensics
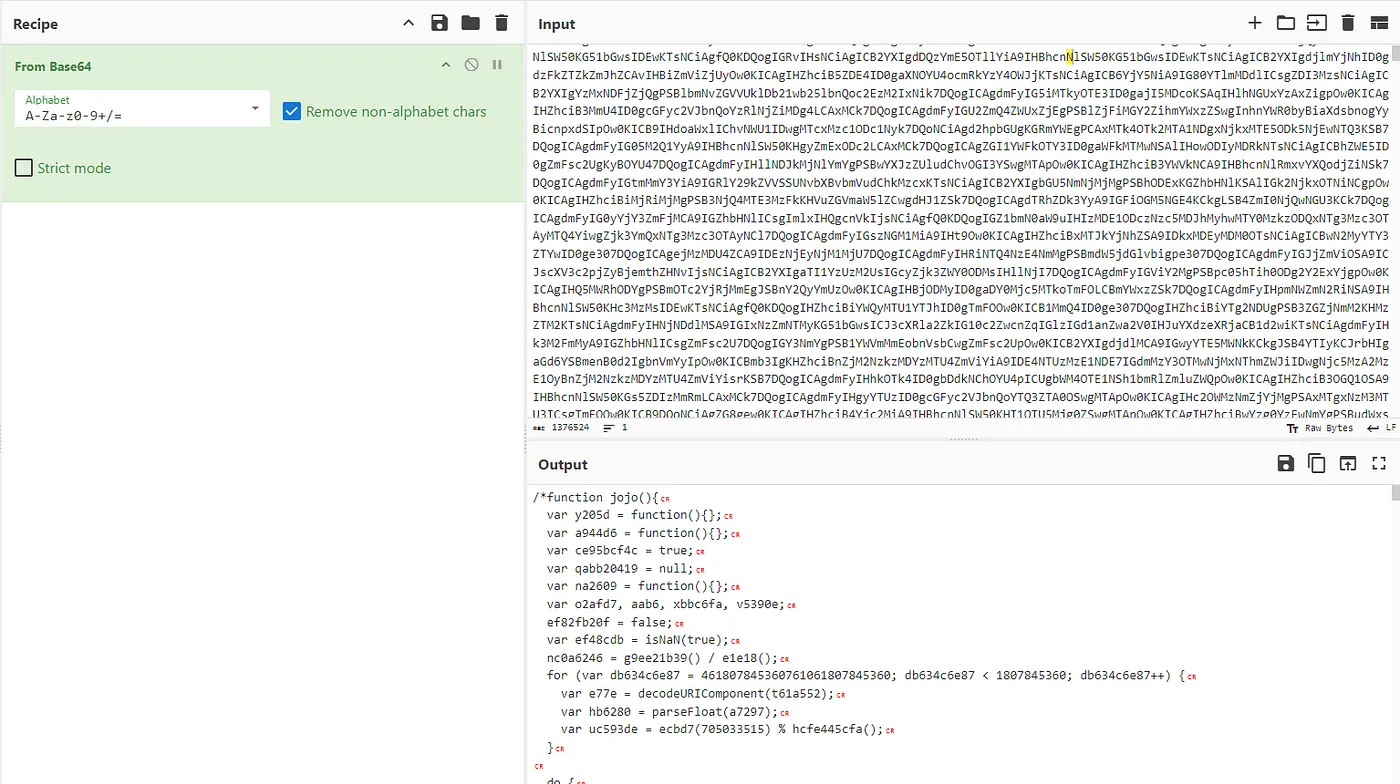
Similar to the challenge above, but this time the contents is a large chunk of base64 encoded data. The task is to get the website of the referrer.

Let’s copy this whole thing and hop on to Cyberchef to decode. We’ll see it’s an obfuscated JavaScript code. It’s a whopping 7k+ lines of code. Initially I tried running it, but I get no result, and trying to figure out if this code has bugs or just for distraction is time consuming.
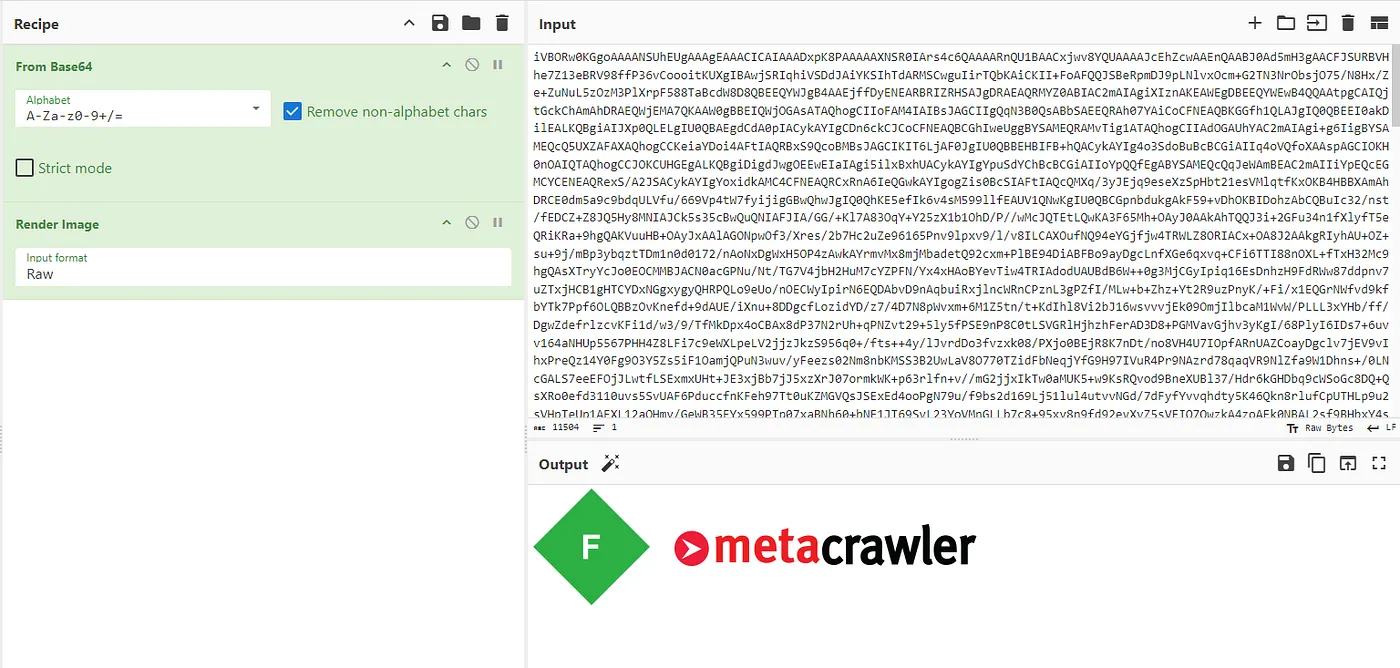
I then discovered at the very last line, another base64 encoded text. It turned out to be an image, and this is what we’re looking for! Let’s just look for their website.
Blank File 1
============
Forensics
We receive an empty Excel file. Let’s unpack it and see what’s it hiding
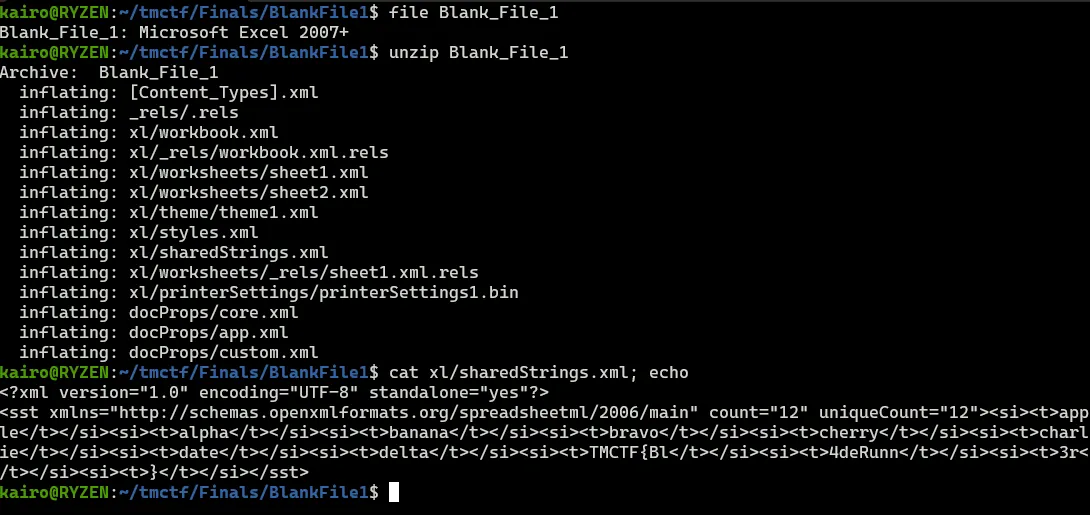
The flag is in plain sight, just formatted in XML.
Packet Snatcher
===============
Forensics
We receive a Packet\_Snatcher.pcap file and our goal is to find the name of the image attached to the email. We fire up **Wireshark** to analyze the network traffic and immediately caught my attention was the unencrypted communication at a mail server, following the TCP stream we see this.

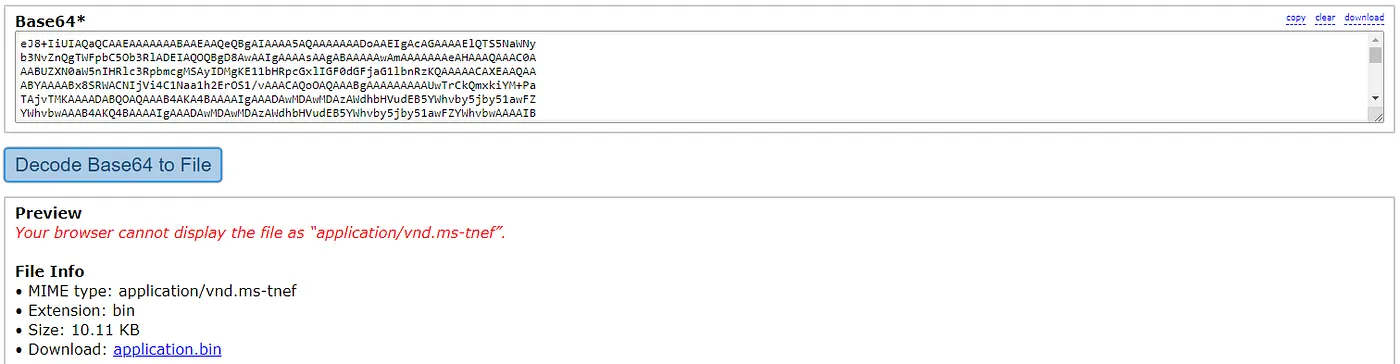
I copied the base64 encoded content of **winmail.dat** and paste it on a website that turns it into a binary for us so we can recover the original file for further forensics.
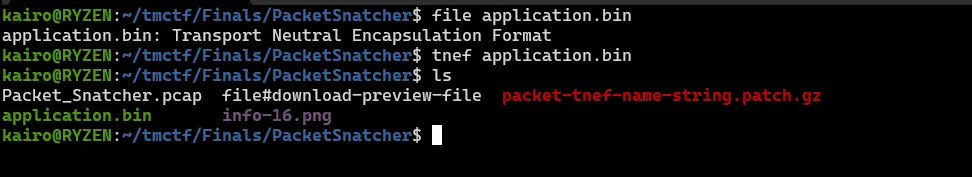
The winmail.dat is in the format of _Transport Neutral Encapsulation Format_ which we can easily extract the contents using a tool using **tnef.** Immediately we see that **info-16.png** is an image attached within the email.
Mystery GUI
===========
Reverse Engineering
We receive a mysterious GUI binary named **MysteryGUI.exe**. It seems to be asking for a password, let’s open **Ghidra** and check the source code for any potential passwords.

In the list of functions, we see a CheckKey function which may be the mechanism behind this executable.
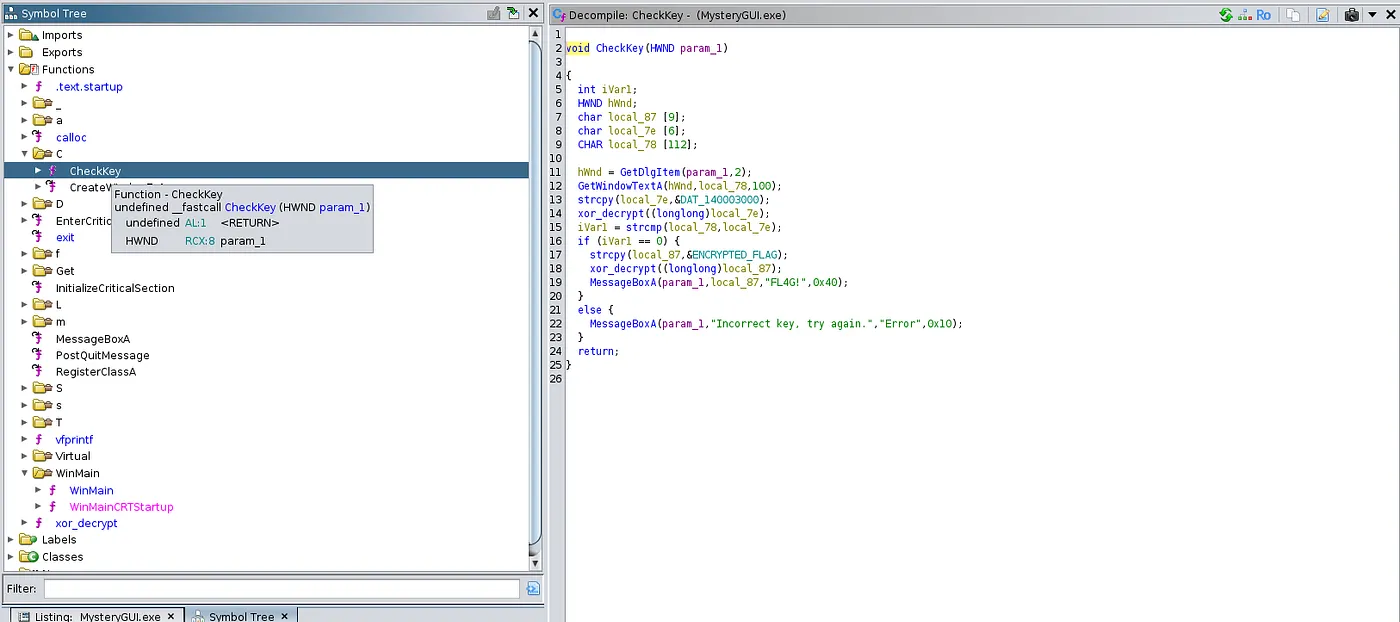
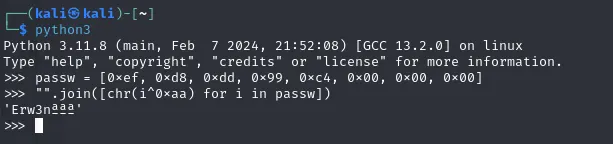
We also find another function named xor\_decrypt which is a XOR cipher using the key 0xAA. This cipher is symmetrical, meaning we can decrypt either the password or flag using the same key.
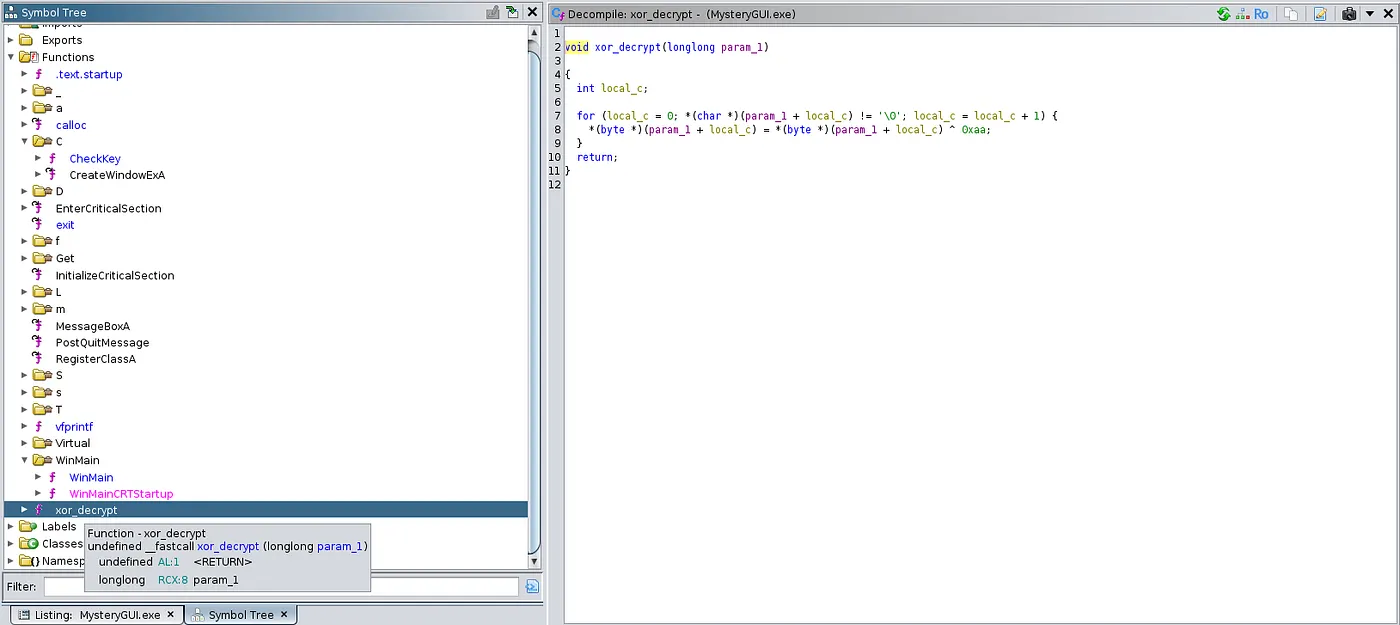
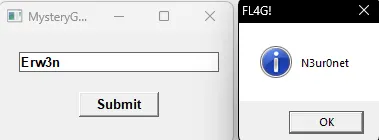
Since the flag gets decrypted by the executable if the correct password is supplied, let’s just manually decrypt the password since it’s also shorter.
[=] Conclusion
================
Thanks for reading this far! Despite not winning this competition, I’m still thankful to Trend Micro Careers Philippines for letting us experience these kind of competitions. I also thank them for giving me permission to create and publish writeups of their competition. See you soon folks!:)